Over the weekend, we were alerted to a significant spike from normal baseline of Twitter links being shared in terrorists WhatsApp group channels. Our product, MORSE, logs in real-time WhatsApp terrorists group channels. It also logs hundreds of other illicit group channels on the WhatsApp platform. Currently we are real-time logging 200 WhatsApp terrorist group channels.
We drilled down into our data logs for the anomaly and found that terrorists have again manipulated social media platforms to post and share their propaganda. There are several terrorist WhatsApp group channels dedicated exclusively for teaching others how to spread the propaganda on social media. The goal here is for them to avoid social media accounts that are being suspended and having their propaganda be removed. Furthermore, they have discovered this new method reaches a much larger audience than other methods they have used. In one screenshot below a Twitter account being used has over 3 million followers.
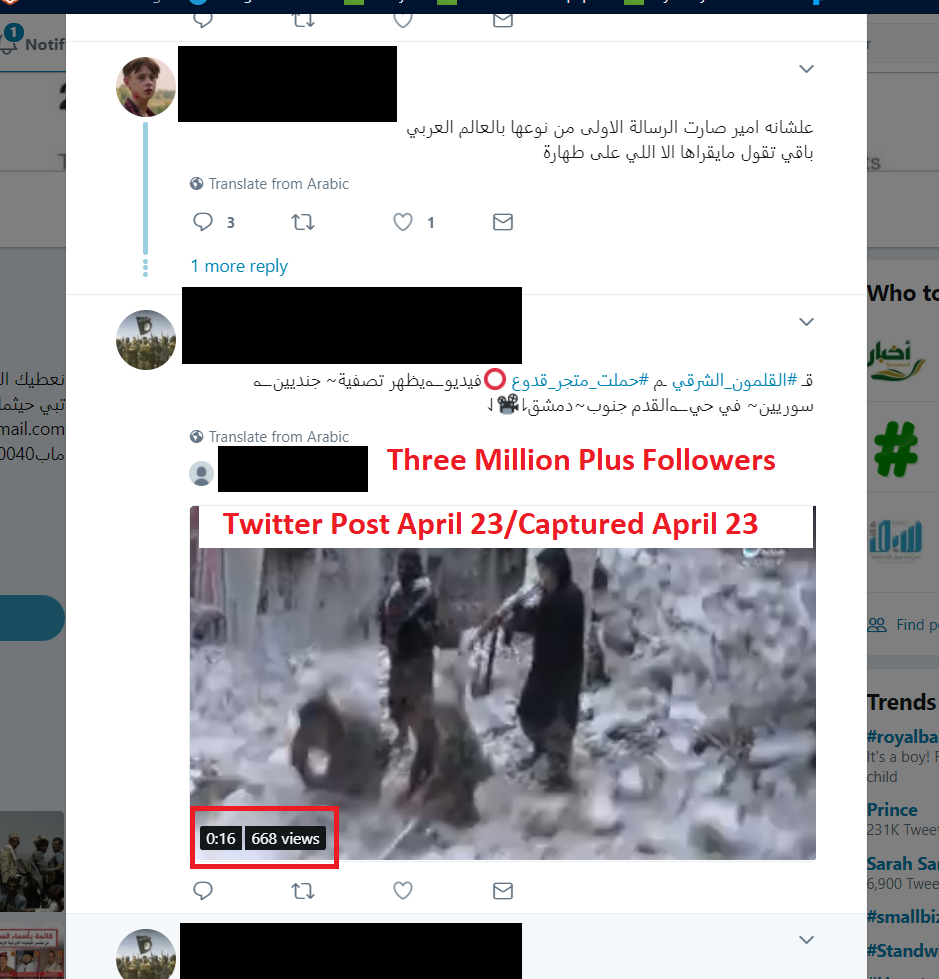
The social media scheme being shared by the terrorists is as follows: 1. Identify legitimate news media and political Twitter accounts with millions of followers. 2. A list of Twitter accounts identified are then posted in the terrorists group channel. 3. Create the propaganda for dissemination as an image, video or audio file and upload it to a file sharing site for others to download. 4. Identify the legitimate Twitter account’s latest tweet posted with the highest count of replies. 5. Scroll down to the bottom of replies and on the last reply, post the propaganda for dissemination. 5. Copy the link to reply and share it on other Twitter accounts or platforms such as Facebook and Google etc.
This method is gaining traction as the propaganda posts still exists, successfully averting social media protocols for identifying such content. We have identified graphic content that was posted several days ago still being shared in WhatsApp other terrorist groups.
We are committed to eradicating this type of content through technology and innovation. Technology tools used by terrorists have been adopted by many of the underground cybercriminals. We all know that Telegram and WhatsApp are commonly infested with such terrorist propaganda. Both Apps have emerged as the new frontier for black market vendors and buyers. A year-to-date analysis of our data (two terabytes) logged real-time from Telegram and WhatsApp shows an increase of approximately 130% from this time last year. Illicit transactions, money laundering, terrorists planning, and recruiting human trafficking offerings on WhatsApp and Telegram dramatically out number the illicit offerings from the Tor darknet black market and forums. Tor’s cybercriminal forums indeed are still actively used by many attackers as well as terrorists to acquire and/or develop their cyber arsenal.
The epidemic of illicit transactions migrating from Tor darknet to social media darknet platforms like WhatsApp is astounding. Users of such encrypted peer-to-peer messaging apps no longer require the sophisticated OPSEC methods used on Tor. Additionally, the consumer audience is now tens of millions on WhatsApp and Telegram respectively compared to approximately two-million Tor users. Of the two-million Tor users, only a small percentage use Tor for illicit transactions.
WhatsApp is very interesting in that it requires a phone number to have an account. Terrorists have figured out that accounts can be established with free VIOP numbers. There are also many extremists and criminals that use a burner phone or their actual personal mobile number. Case in point, the events in this article for Twitter posts have been identified by us to be originating from a mobile phone provider in Sweden. In fact, many of the group members of this WhatsApp channel for Twitter posts are originating from Europe Union countries, the Middle East and the United States.
What can social media and technology companies do to eliminate such content? For starters they can begin by swallowing their pride and accepting that third-parties have solutions available to help them. Next, they must accept that not all third-parties have the ‘silver-bullet’ solution that can justify their PR statements of “doing all we can”. Of the social media companies we offer to assist, the standard protocol is to be satisfied with current vendor relations. The other option is to choose to address the matter internally. Neither of the choices are enough. The case of the Twitter posts is a great example showcasing an attack being planned in the posts.
What then, should social media do when more people die senselessly because social media giants like Facebook, WhatsApp, Twitter and the like believe they can fix the problem? This is not a case of compromised logins or user’s personal data being resold. Actual human beings are being killed because social media is not compelled to proactively remove the content on their platforms. If 200 plus terrorist channels with 255 members in each channel is not enough for Facebook and WhatsApp to take action, then what is?
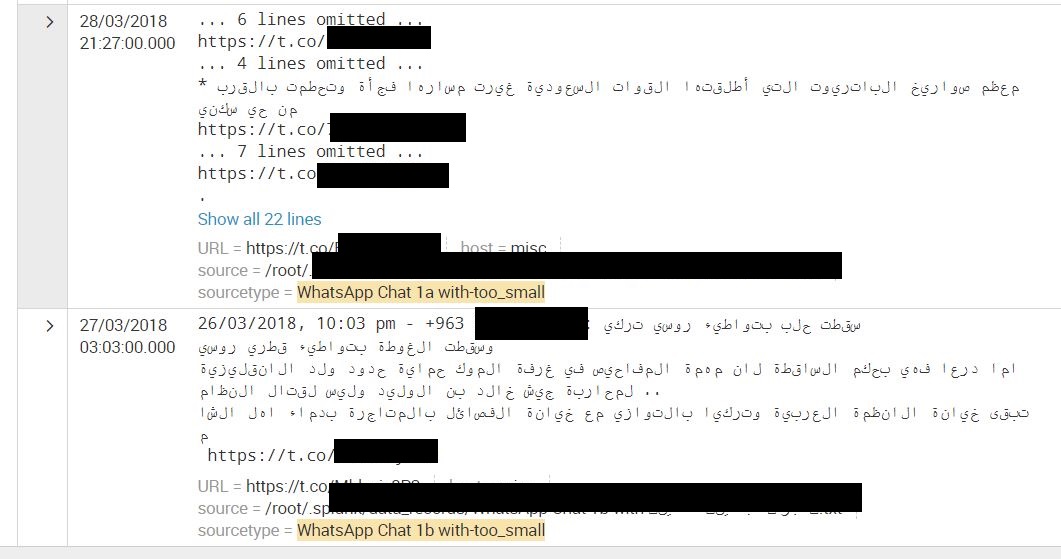
BLACKOPS Cyber WhatsApp Log Example
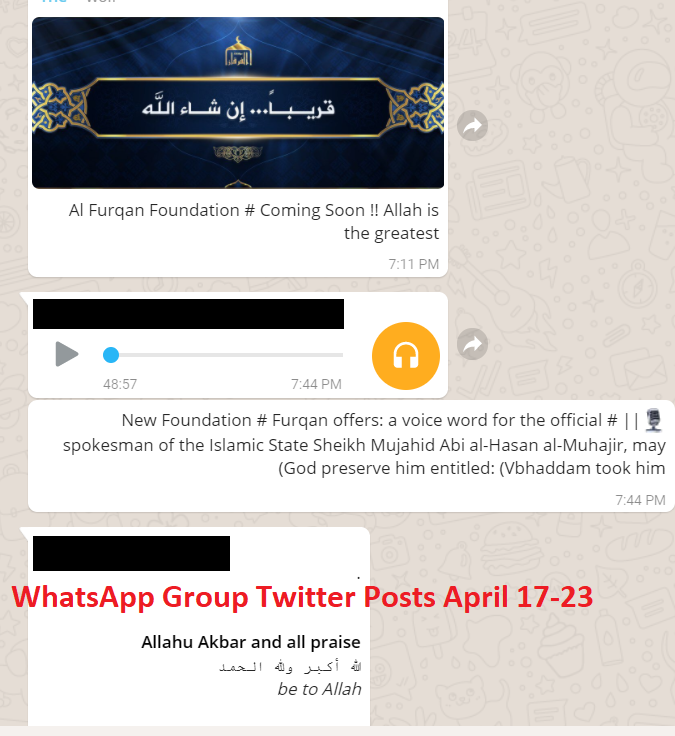
WhatsApp Twitter Group
Tags: BLACKOPS, Cybersecurity, Darknet, Hacking, IT, Propaganda, Social Media, Technology, Telegram, Terrorism, TOR, Twitter, WhatApp


