Cyberattacks and data breaches are part of our day-to-day life, so much so, that people have become desensitized to these events. In every case, the customers’ compromised data recompense is “credit monitoring, free for one year”. We have often heard people joke about how many free credit monitoring packages they have due to the high number of data breaches their information was connected to in a 12-month period. Ten years ago, the darknet/deep web was unheard of compared to the buzzword status it has achieved, as it is a common term heard on television and radio. As recent as 2014, there were only two commercial entities offering Darknet Intelligence (DnI).
Currently, choosing a DnI provider is akin to buying a bottle of water; so many brands and prices for the exact same thing – water. Many DnI providers are packaging the same data sourced from crawling/scraping sites or human analysis by logging into darknet black markets or forums, sifting through the latest posts. Some DnI providers claim to index millions of pages every day from darknet sites by scraping. Scraping is possible for some darknet sites, but not all.
Experience has taught that the best intelligence is found in invite-only Vetting Required Membership (VRM) darknet sites. VRM sites generally have less than one hundred members and an anti-bot-scrape code. Anti-bot-scrape code identifies a scrape instance occurring, then instantly bans the scrape and user-id access, thus ceasing the scrape.
Darknet Intelligence Secret:
DnI providers omit disclosure to clients that scraping cannot bypass all login pages to capture content. Not all darknet sites are using CAPTCHA as an authentication method, especially the quality darknet sites. Authentication can be a randomly generated equation, a trivia question, or combination of both giving a limited time to input the correct answer. We have seen VRM sites that require a darknet history question be solved for authentication e.g. “What new site did TCF admin launch?” This darknet history question pre-dates the existence of most DnI providers back to 2014.
Therefore, scrape methods are often indexing a login page yielding zero actionable intelligence. Concluding, companies using scrape methodologies are likely returning the same results.
Since 2015, numerous DnI companies have launched, all competing for the same market space. Indeed, a competitive marketplace stimulates innovation, always striving to deliver the best product for the end user. However, DnI is stigmatized as being a murky abyss with stats that challenges us to comprehend the unknown. The fact of the matter is although the deep web is estimated to be 400 times larger than the indexed internet that you know and use daily, the darknet makes up only a fraction thereof.
Tor Sites
As of March 2018, there are approximately 70 thousand TOR sites, down from Spring 2017, where the number of TOR sites peaked at approximately 120 thousand. Furthermore, as of this writing (30 March 2018), there are currently 6,291 peer routers in TOR network. A TOR connection requires 3 random routers to connect to every 6 minutes, “entry guard > relay > exit node”. The Probability of a consecutively similar combination is 1-in-41,515,940,466.
Stand-alone DnI providers can best serve clients by disclosing that they can only provide a piece of the puzzle. Augmenting stand-alone DnI with other DnI sources is a unique concept, albeit exactly what intelligence is: verify, verify, verify. We discovered that, augmenting with other DnI providers, all parties retained their respective proprietary IP while simultaneously enriching the clients DnI visibility. DnI is unlike conventional cybersecurity products in terms of threat events monitored; cybersecurity products secure their clients from perimeter surface net attacks among many other vectors, while DnI attempts to provide timely intelligence from anonymous peer-to-peer networks.
“Two typical Darknet types are friend-to-friend networks (usually used for file sharing with a peer-to-peer connection) and privacy networks such as Tor.”
Many DnI providers purport to have billions of compromised data records, a statement which is highly likely. However, 98% of those records are re-mediated. Antiquated known data leaks are free for download and great for research. Actionable DnI is the unknown here and now.
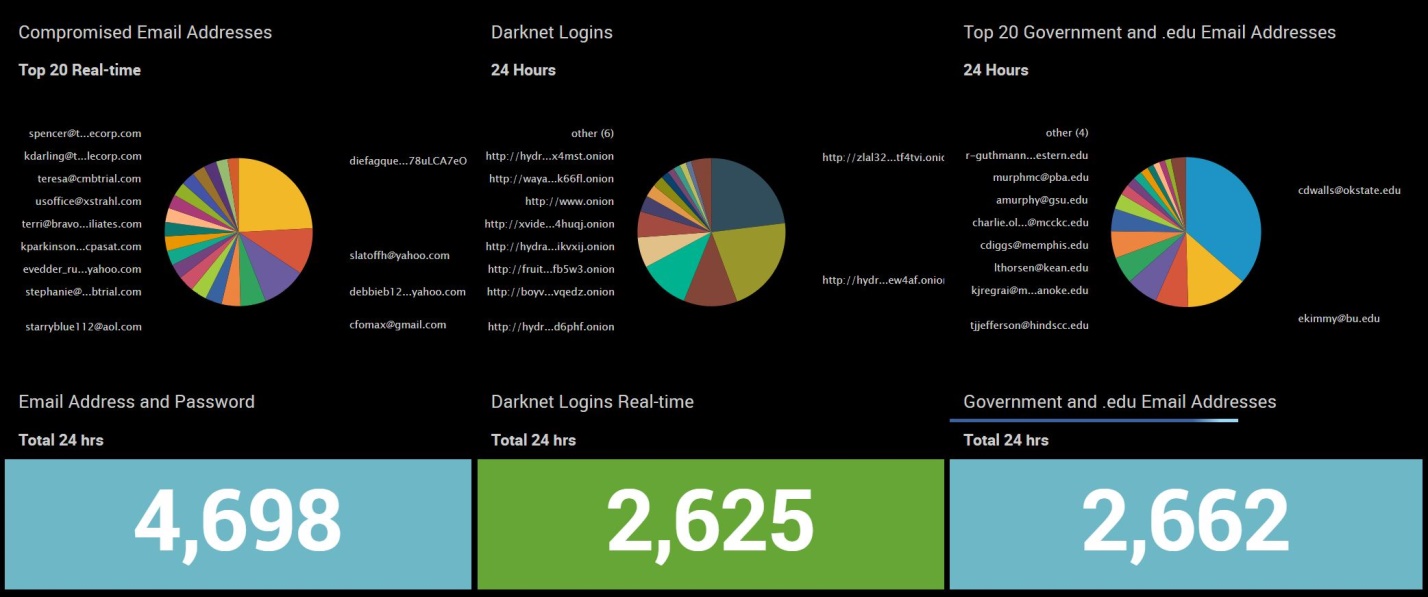
In this series, we will be sharing the darknet threats we are seeing in real-time with timestamps, screenshots and description. We will kickoff this first article with unique never before seen compromised email addresses and passwords including .gov and .edu domains. Additionally, threat actor login credentials for darknet black markets and forums.
Tags: Actors, Attack, Breaches, Compromised Data, Computer, Cyberattacks, Cybersecurity, Darknet, Darknet Sites, Data, Data Breaches, Data Leaks, Deepweb, DnI, Email, Information, Intelligence, IP, Malicious, Methodologies, Networks, Password, Risk, Secrets, Security, Threats, TOR, VRM


