The CSO Conference & Awards: A Brief History
Blockchain Technology: From Hype to The Future
Tools to Meet Tomorrow’s Mobile Cybersecurity Threats for Government
Account Takeover Fraud: Navigating the Treacherous Digital Waters
The Importance of Jailbreaks for iOS Security Work
{Latest Posts}
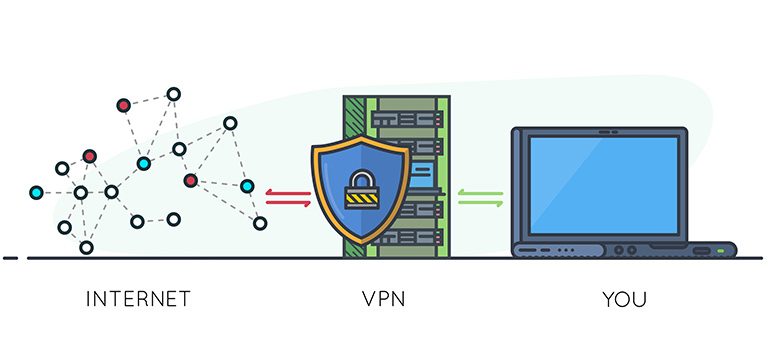
A Weak VPN Could Be More Destructive Than No VPN
In the present era, an individual’s privacy solely depends on internet security. Your banking details, your pictures, and other sensitive information are available on different channels such as social media accounts, websites, and other online

The Importance of Protected Digital Assets
A significant number of your digital assets, whether personal or professional, are now digital in this current age. The transfer of business practices, records, and even storefronts from a mostly physical world to a digital

Why Software Architecture Matters in Foolproof Cybersecurity
The long-term success of any business or digital venture depends solely on a strong software architecture – one that has robust performance and is equipped with foolproof cybersecurity. In simpler terms, software architecture forms the

(In)Famous Hacking Groups
The Different Hacking Groups Hacking Groups are a staple of cybersecurity culture. Since the 1995 release of the movie Hackers, there has been a very specific subset of cultural cliches we associate with all hacking

Cognitive Computing for Business Insights and Gains
We live in an age where logical reasoning matters the most, whether we use apps on smartphones for weather forecast, or software for improving driving. Ever since the invention of computers, we have grown to

Catfishing: Not Just About Money
We live in a time where it is easier than ever to deceive people. For example, the internet now enables us to speak anonymously through message boards, comment sections, and even online games. Additionally, the

Cyber Threats: Why Cybersecurity Is More Important Than Ever
The age of digitization has led to many significant changes, both in our day-to-day lives and larger scale operations. One such example is the nature of terrorism. In the last decade or so, a new
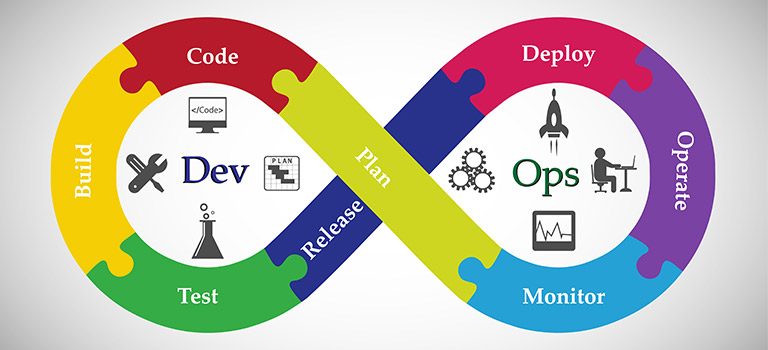
DevOps Market: Novel Approaches & Products
How to Bring a Boom to the DevOps Market With competitive pressure increasing drastically and the digital economy progressing considerably, enterprises need to figure out new ways to plan, develop, and add value. Therefore, to






