The CSO Conference & Awards: A Brief History
Blockchain Technology: From Hype to The Future
Tools to Meet Tomorrow’s Mobile Cybersecurity Threats for Government
Account Takeover Fraud: Navigating the Treacherous Digital Waters
The Importance of Jailbreaks for iOS Security Work
{Latest Posts}

5 Common Cybersecurity/IT Mistakes in Your Small Business
The world is filled with hackers and other criminals who hunt the web for unprotected small and medium-sized businesses. Cybercriminals understand that many businesses are not equipped to manage a breach, leaving them more vulnerable

The State of Server-Side Request Forgery Risks in 2022
Perhaps one of the best Black Hat talks in recent years was renowned web security researcher Orange Tsai’s presentation about bypassing Server-Side Request Forgery (SSRF) defenses. Together with his team, Tsai proposed a “very general

Why Data Protection Must Be a Part of Every Cybersecurity Strategy
Widespread transition to remote/hybrid work creates vast opportunities for cyber attackers. With much more data being stored in the cloud and employees toiling away in less-secure home-office environments, ransomware attacks have skyrocketed. All told, ransomware

Application Security Should Be A Badge Of Honor, Not A Wall Of Shame
Cybersecurity news is a curious thing. For the most part it’s bad news. Companies have been breached, risks are ever increasing and another billion-dollar crypto raid is under investigation. Feels like we have enough to

Fixing Vulnerabilities at Speed—How Engineering and Security Can Achieve True DevSecOps
What happens when two distinct teams with varied technological expertise, different incentive structures and contrasting priorities converge?—the answer is usually tension. During a recent discussion with colleagues, a completely different result was experienced. ‘Camaraderie’ is
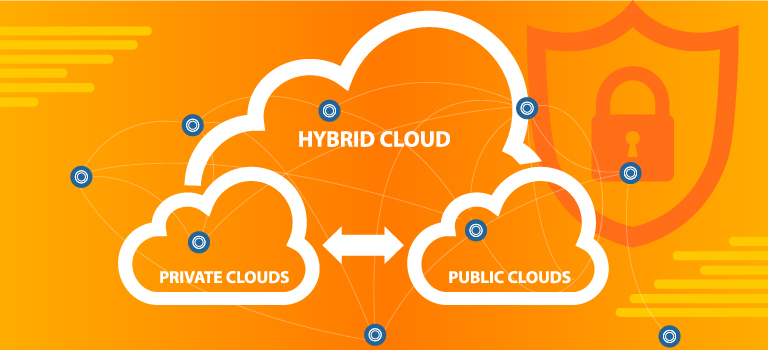
Addressing the Challenges of Securing Hybrid Cloud Access: What You Need to Know
For a growing number of companies, a blend of public cloud services, private clouds, and on-premises infrastructure offer the best solution to the benefits and limitations of each. Cloud adoption is growing, and the past
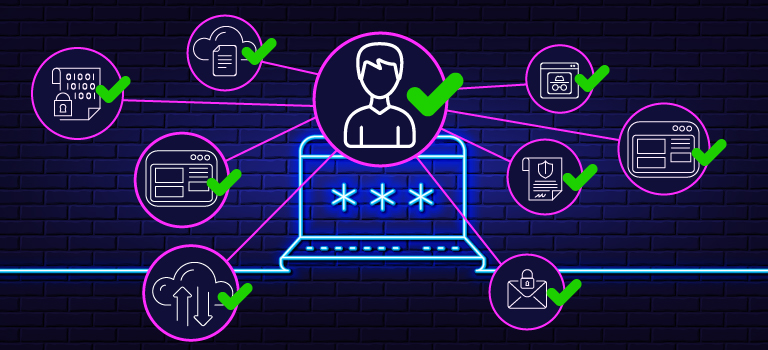
Single Sign-On: Balancing Power and Responsibility
Single Sign-On (SSO) is a powerful productivity tool for organizations today. Facilitating access to on-premises and cloud-based applications, it dramatically simplifies the user experience. With SSO, users simply logon once, open a web browser or

Why it’s Time to Adopt a Risk-Based Approach to AppSec
Today, AppSec (Application Security) is not only about compliance with regulatory frameworks. In the face of newer threats, a growing attack surface, and the lack of AppSec talent, legacy WAF solutions and traditional security approaches






