Speed, Velocity, and Acceleration. The physics of motion are well documented, and we understand how these scalar and vector quantities differ. In information security and cyber risk management the dynamics are not as well understood which has confused our ability to distinguish between motion and progress. This confusion intensifies our escalating risk cycle by causing a mirage of control that continues to lead us down a path of compromise and catastrophe, adding not only to our growing cyber labor shortage but also generating greater societal cyber risk implications.
Let’s start with some basics on the physics of motion. Speed is a scalar quantity which is a measurement of magnitude regardless of direction such as 55 MPH. In the cyber context a measure of motion would be things like patching hygiene levels, time to detect, time to contain, or a wide variety of other vulnerability management and attack surface measurements traditionally used in our security operations as well as board reporting on how well we are doing with respect to our cyber defenses.
The problem with using these types of measurements in the cyber context is that we are confusing motion vs. progress. This is a focus on motion which leads to more of the same broad-based spray and pray approach. We create goals for ourselves to: patch faster, monitor more, reduce time to detect, reduce time to contain. While these have added some value, they have also added to an increase in our total cost of controls, and in some cases created a false sense of security in addition to an inaccurate portrait of the actual state of risk.
Vector quantities are a better approximation
of progress because they include not only
magnitude but direction such as 55 MPH Northeast.
To achieve real progress in cybersecurity, we need to have measurements that are vector quantities like velocity or acceleration. Vector quantities are a better approximation of progress because they include not only magnitude but direction such as 55 MPH Northeast. So, now we know where we are headed in addition to how fast we are getting there. In the cyber context of having not only the direction, but more importantly the proper coordinates providing specific proactive direction where action can be taken to mitigate risk, is challenging but not impossible.
In the cyber context, this would be things like understanding pre-breach and the anatomy of attack so that points along the entire attack path can be understood and actions can be taken to break the attack paths that exist. This sort of attack path reduction is where we can demonstrate real risk reduction because steps have been taken that reduce attacker opportunities, not just on an initial point of compromise, but on the entire attack path that leads from that initial foothold through our organizations to a point of material impact such as the loss of sensitive IP or PII, or a critical system taken offline.
Understanding these attack paths with speed would be a time to context measurement. Breaking these attack paths and prioritizing detection and response controls along these attack paths would accelerate our proactive risk mitigation due to the specific direction (coordinates) provided.
So, how do we reorient our entire security operations function so that it is optimized to handle the volume of activities it is responsible for? How do we reposition ourselves from an anchor point of continual reaction to one where our SOC can take proactive action in front of the cycle of risk?
The heart of these changes is a redefinition of the risk equation we have been using for decades.
FROM: Risk = F (Threat, Vulnerability, Consequence)
TO: Risk = F (Threat, Exploitability, Consequence)
But first we need to realize that vulnerability does not equal exploitability. Secondly, we need the capability to easily map these attack paths and understand the exploitable pivot points that lead from the initial foothold or point of compromise through our environment to the catastrophe that causes material impact to our organizations and our customers. When both conditions are met, we can optimize our security operations shifting from only an anchor point of reaction to one of proactive cyber risk management. (See Figure 1 below)
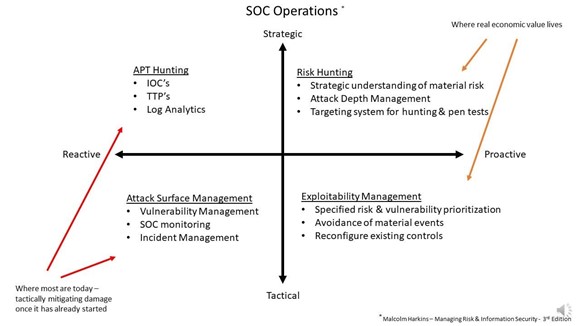
Security Operations (Figure 1) can be framed according to a simple framework.
On the vertical axis we can categorize our work from tactical to strategic. Being strategic means that we are doing what is necessary relating to the identification of the organization’s long-term interests and we have the means of achieving those interests. Our organizations strategically want a bend in the curve of the risk they are experiencing as well as a reduction in the total cost of controls. Both of which have been growing for decades.
On the horizontal axis we can categorize our work from reactive to proactive. Proactive means creating or controlling a situation by causing something to happen rather than responding to it after it has happened. So being proactive by almost every implication would then lower risks and lower costs, especially if you had the specific coordinates (devices, identities, applications, network segments) within your enterprise to break attack paths before an event occurred.
So why then are most security operations anchored in tactical reaction with some limited strategic reaction activities such as APT hunting? Many would argue it is due to resource constraints. They don’t have the budget, don’t have the talent, and don’t have the tools. While this may be true in some cases, consider that we are in this situation because of the paradigm with which the entire security industry has been built.
In the world of cybersecurity, the most frequently asked question focuses on “who” is behind a particular attack or intrusion – and may also delve into the “why”. We want to know who the threat actor or threat agent is, whether it is a nation-state, organized crime, an insider, or some organization to which we can ascribe blame for what occurred and for the damage inflicted. Those less familiar with cyber-attacks may often ask, “Why did they hack me?” Rest assured that we have no real influence over threat actors and threat agents – the “threat” part of the above equation.
These questions are rarely helpful, providing only psychological comfort, like a blanket for an anxious child, and quite often distract us from asking the one question that can really make a difference: “HOW did this happen?” But even those who asked HOW – have answered with simple vulnerabilities – we had an unpatched system, we lacked MFA, or the user clicked on a link.
Those less familiar with cyber-attacks
may often ask,
“Why did they hack me?”
The current focus on the WHO, WHY, and HOW based on vulnerability does the industry and everyone else in general very little service. As mentioned earlier, we need to rethink and refocus the Security Risk Equation to examine the complex details of how attacks really occur to prevent them in the future. We need to have a continuous offensive perspective for our defense controls.
The primary variable in the security risk equation is having the maximum chance to impact risk where an organization is exploitable.
From a consequence and impact perspective there are only three primary consequences we need to focus on: Confidentiality, Integrity, and Availability (CIA triad). Each of these have different potential impacts to an individual, to an organization, or more broadly to society depending on the technology or data attacked. When we examine “how” attacks are accomplished we see three core targets for attacks:
- Attacks on identity credentials
- Attacks focused on the execution of malware
- Attacks that create a Denial-of-Service (DoS)
So what must always be analyzed, acted upon, and reported to management on is HOW an intrusion or attack could be successful, so we can provide prescriptive recommendations on how to eliminate attack paths as well as where to prioritize detection of anomalous activity to intercept attackers before a material event occurs.
At Epiphany Systems we set out to solve this problem which resulted in a transformative capability that predicts not only the initial point of compromise and how it will bypass your current endpoint controls but also detailing the entire attack path that any adversary would most likely use for an attack PRE-BREACH. In doing so, we illuminate the complete exploitability of your entire organization, not just the exploit of a simple vulnerability that an attacker would use for an initial foothold. Our recommendation engine tailors specific actions that can be taken to break any spot along the attack path before it occurs. Our goal is to enable security operations to take proactive steps tactically and strategically to lower your risks at a lower total cost.
T. Dewar the famous Scottish distiller once said, “Minds are like parachutes, they work best when open.” You are invited to open your minds and imagine a new paradigm for your security operations, a new approach to manage and measure risk with exploitability as the fulcrum of this transformation. ![]()
Malcolm Harkins



Leave a Comment