Question: Can infrastructure play a positive role in your Cybersecurity program? Most often we think of infrastructure in a negative way, something we have to protect. It is the mess that we have to attempt to control through policy, procedures, technology and training. It takes a lot of different systems, network and data security components to “secure” a corporate infrastructure, all which raise complexity and associated cost. What if you could deploy a tested and proven technology that would reduce complexity, reduce costs and reduce threat vectors all at the same time? Would it be worth it? Would the fact that it comes out of the classified space make you think twice?
Let’s take a look and you can make up your own mind.
Known many years ago as Multiple Level Security (MLS) and now known primarily as Cross Domain Systems (CDS) many of these solution sets have at their core a trusted operating system. Trusted operating systems got their start in the Department of Defense. In this case trusted means tested and verified as secure according to a strict set of standards and rigorous testing. Over time trusted operating systems became a de-facto requirement for security solutions that permit access to multiple levels of classified network (ex. Secret and Top Secret) from a single access device. The access device can be in the form of a user desktop, laptop or thin client. Today, these cross domain access devices are in use throughout Intelligence, DoD, Civilian and Law Enforcement agencies providing secure access from a single device to multiple classified and un-classified networks. At their core they provide access to each network and the user’s approved assets in that network. They also deny cut and paste, drag and drop and other forms of information movement without interaction with approved subsystems designed specifically for that task.
So you are not at a Government or Law Enforcement agency with classified network and you are asking “Why should I use this solution?”, “It sounds like overkill and it must be complex.” I suggest it is not.
Looking at each you will find COTS (commercial off the shelf) products and reuse of your existing components:
- Distribution Console – Trusted OS — RedHat Enterprise Linux with Security Enhanced Linux components
- Your existing – Network, Directory Services, etc.
- Your existing – Desktops, Thin Clients or Laptops
- Access device – Read-Only Secure OS — Security Enhanced Linux
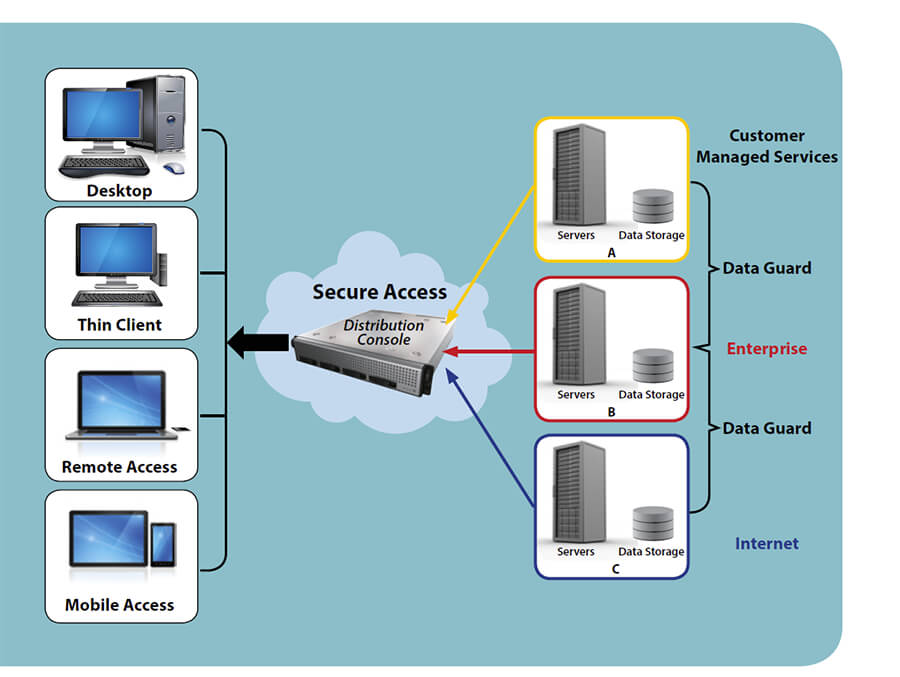
The combination of these components implemented in a corporate infrastructure permit the highly secure segmentation of networks by sensitivity/label. You could, as seen in the following example, segment the Internet, enterprise network and customer managed services networks. You could also do further segmentation of the enterprise network into logical, restricted access groups such as Corporate, Legal, Finance and R&D, etc. The following is an architecture example:
This solution includes two primary components, a distribution console and the client software. The distribution console provides stringent security controls and maintains network/data separation. The client software (a client side version of the trusted OS) communicates directly with the distribution console. Each network has a separate physical network interface on the distribution console that is assigned a security label which further protects from unauthorized access.
Regardless of the form factor, the client side software ensures that the client endpoint runs a read-only, stateless secure OS. The layer on top of the secure OS is the security-enabled and labeled (visual and code-based) graphical windowing system that provides access to simultaneous presentation layer clients (per identified network). The windowing system also provides for client-side rendering of streaming multimedia protocols.
So now you have access to the Internet and the securely segmented enterprise and managed services networks. But that is it, secure access. Most Corporations cannot live on just access to networks. Corporations must share information and data to plan, collaborate and bill for services. So what do you need to securely transfer information from, as an example, the Internet to your enterprise network without introducing the threats you just got rid of by implementing a trusted infrastructure?
To securely move data between networks we need to add one more trusted and proven component, known as a guard or transfer technology. Guards also make use of a trusted OS, strict data transfer policies and virus/malware detection. Guards offer automated secure transfers of data from one network to another. The Guard sits between the two networks and permits Bi-directional traffic which is tightly controlled through the rule sets and security controls contained within the guard and the trusted operating system on which it runs. Most guards available today support customized rules that can be used to validate data for each network that, as data is received, the rules filter the data and look for the tags that direct where the data can be sent ensuring that it is not misdirected or compromised. Through customized policy and rules sets, a Guard can manage vast amounts of complex data streams across multiple networks with extremely low latency.
So in this example we have securely segmented critical enterprise networks. A breach or malware on one network has a higher level of containment than available using current market products. At the same time, we have guard technology to permit information sharing and collaboration as permitted by policy. For reducing threat vectors, we are introducing and making use of COTS and open source trusted operating systems integrated with our existing networks, systems and storage platforms.
As to cost, it fits well within technology refresh cycles and cyber budgets. Implementation and management are much lower for your enterprise than you may have heard about from Government implementation.
If your current cyber policy, procedures, training and technology have created a four foot wall around your enterprise, cross domain solutions can raise that to an eight foot wall. Consider your layers of protection in case of cyber attack.




Leave a Comment