Revisiting the Cyber Kill Chain
The Cyber Kill Chain is considered a benchmark for cyberintrusion detection. It is functionally analogous to the Terrorism Kill Chain in all but one respect.1
Intrusions are now a much broader problem class than they were when the Cyber Kill Chain was developed. However, if hackers tend to use trend-focused approaches, then that functional gap closes considerably with the application of strategic-level counterterrorism (CT) techniques.
Current intrusion detection techniques focus on system vulnerability, and therefore determine immediate threats and not strategic patterns. The cyberthreat environment requires strategic-level analysis of the broader threat, including emerging tactics, techniques, and procedures (TTPs). For strategic-level data collection, vulnerability-focused systems – such as those which focus on injection vulnerabilities or simple security misconfiguration – are insufficient on their own.
Modeling the threat ecosystem strategically through the lens of counterterrorism techniques will enable earlier detection of anomalous behavior. In order to get ahead of the threat, cybersecurity firms must integrate counterterrorism-trained personnel.
Campaign Analysis vs. Statistical Analysis
Statistical analysis and rule-based analysis, two methods focused strictly on system vulnerabilities, are insufficient for discovering and mitigating advanced persistent threats (APTs). Neither statistical analysis nor rule-based analysis is capable of detecting attacks which may occur over an extended period of time.2
Campaign analysis in cybersecurity is identical in scope and practice to strategic-level counterterrorism analysis. Because the Cyber and Terrorism Kill Chains are essentially analogous, information gained from cyber campaign analysis will be behaviorally equivalent in the Terrorism intelligence cycle. In both cases, broad-scope analysis over time will identify aggregate patterns and reveal overlapping indicators, identifying and eventually predicting emerging and evolving threats. This creates a viable argument for the inclusion of counterterrorism-trained intelligence personnel in strategic intrusion analysis (SIA) teams.
Given enough aggregate attack data, it would be possible to apply game theory toward persistent cyberattackers, forcing them to change specific and predetermined vectors at points of their attack cycle on subsequent intrusion attempts, which we can then detect or mitigate progressively earlier. The functional gap here is that cyber-attacks evolve faster and in larger leaps than terrorism methods. But if the data is out there, and is collectable, then applying strategic counterterrorism tradecraft can have a profound effect on the cyberthreat ecosystem.
Intelligence Gaps and the Intelligence Cycle
Intelligence drives operations, and cybersecurity operations must be geared toward collecting attack data in addition to stopping attacks.
The purpose of a military intelligence analyst is not to find answers, but to determine further questions. As intelligence gaps are filled, analysts determine new gaps, and the process begins anew. This “peeling of an onion” can be a difficult concept for civilian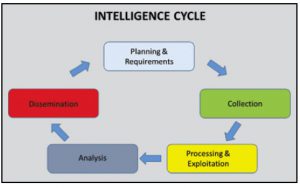 analysts to grasp, particularly “business intelligence analysts” whose jobs revolve around quantifiable and incontestable data. It is likely even harder for many executive-level consumers to appreciate, and may create a point of contention. However, gap analysis drives the counterterrorism intelligence cycle, and it must do so in a Strategic Intrusion Analysis (SIA) cell. The SIA cell should function in the same manner as an intelligence cell, with the resolution of intelligence gaps as the fundamental mechanic that drives SIA and cyber operations.
analysts to grasp, particularly “business intelligence analysts” whose jobs revolve around quantifiable and incontestable data. It is likely even harder for many executive-level consumers to appreciate, and may create a point of contention. However, gap analysis drives the counterterrorism intelligence cycle, and it must do so in a Strategic Intrusion Analysis (SIA) cell. The SIA cell should function in the same manner as an intelligence cell, with the resolution of intelligence gaps as the fundamental mechanic that drives SIA and cyber operations.
By understanding the aggressor’s kill chain, particulary in reference to an APT, the defender can not only thwart the current attack but also detect future attacks earlier and build resiliency into the defensive posture. This is the purpose of intelligence in counterterrorism, and it is directly analogous to APT. This is also why the Cyber Kill Chain model is not necessarily intrusion-centric; it functions just as well with data from unsuccessful intrusions.
In addition to employing the intelligence cycle, other counterterrorism intelligence practices include:
- Preliminary analysis
- Profiling
- Center of gravity (COG) analysis
- Predictive analysis
- Analysis of competing hypotheses
These practices are all readily applicable to cyberintrusion data.
Addressing the Capabilities Gap
IT Professionals Are Not Counterterrorism Experts.
The U.S. military is currently turning out thousands of counterterrorism-trained personnel each year who can be cross-trained in IT methodologies, whether through certifications or on the job. The U.S. military also has mandatory annual training in network defense and cybersecurity best practices for all service members. Experienced intelligence personnel in the IT sector can dissect the threat at the strategic level by analyzing data gained from multiple intrusion kill chains over time, both successful and unsuccessful.
Strategic analysis allows us to understand an adversary’s capabilities, intent, and operational patterns. With the right team, it should be possible to develop holistic, integral network resilience by using what attackers consider their strength – their persistence – against them. Strategic-level APT analysis will also enable broad-scope counterintrusion campaigns.3
Traditional Incident Response Methodology Presupposes a Successful Intrusion.
In order to determine patterns of operation, counterterrorism analysis employs threat 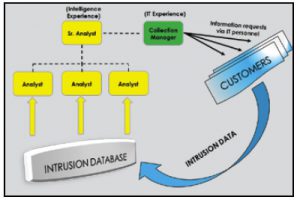 information from unsuccessful attempts as well as from successful attempts. Threat intelligence gained from mitigation and detection efforts – for example, data from a failed broken authentication exploitation – is as valuable in the intelligence cycle as information gained from dissecting a successful attack. Strategic intrusion analysis, fused with CT tradecraft, provides increasing cyberresilience even with successful network defense.
information from unsuccessful attempts as well as from successful attempts. Threat intelligence gained from mitigation and detection efforts – for example, data from a failed broken authentication exploitation – is as valuable in the intelligence cycle as information gained from dissecting a successful attack. Strategic intrusion analysis, fused with CT tradecraft, provides increasing cyberresilience even with successful network defense.
Analytics Don’t Protect Data
Predictive analytics and Big Data play a huge role in managing networks and resources. However, “analytics” is no more than another word for “monitoring.” Security information and event management (SIEM) systems correlate log events from security and networking devices, reducing the security burden and providing insight and attack data that would be critical to a Strategic Intrusion Analysis Cell. But no matter how advanced, analytics on their own do not protect data.4
Risk Management Concentrates on Minimizing Damage
Risk management currently focuses on minimizing data exposure, and often requires making complicated tradeoffs between potential damage mitigation and business demands.5 Strategic-level analysis of intrusion data is fundamental to a mature and robust cyber risk management environment, and will provide executives with a stronger and more calculated set of decision points.
Customers Want a Silver Bullet
There are no magic solutions to network security issues. Strategic intelligence tradecraft does not develop a turnkey product to secure a customer’s data. A Strategic Intrusion Analysis Cell, while not working at the immediate level to stop cyber-attacks, will augment the existing infrastructure of larger IT security firms. A Strategic Intrusion Analysis Cell can alleviate customer concerns and show that your firm is serious about getting ahead of cyber-attackers.
Conclusion
Discussions of APT mitigation and strategic intrusion analysis (SIA) often lack integration of trained intelligence personnel. This is likely due to a lack of formal intelligence training in the IT sector.
SIA performed with counterterrorism intelligence tradecraft will provide cyber-resilience and allow decision makers to incorporate tailored and predictive cyber-resistance into enterprise-wide risk-management and governance processes. Modeling the threat ecosystem through strategic intrusion analysis will enable earlier detection of anomalous behavior and improve your consultants’ understanding of the threat landscape, thereby improving your customers’ overall defensive posture.
Integrating couterterrorism intelligence techniques into strategic intrusion analysis, and hiring intelligence-trained personnel for APT kill-chain strategic intrusion analysis teams, grants a unique opportunity for professional collaboration between military and IT experts. While establishing a Strategic Intrusion Analysis Cell may not provide a direct financial return, the demonstrated dedication to providing the next level of cyber-resilience can establish participating IT security partners as first-tier options for cybersecurity.
Sources
- Hutchins, Eric M., Michael J. Cloppert, and Rohan M. Amin. Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains. Technical paper. Accessed July 15, 2016. http://www.lockheedmartin.com/content/dam/lockheed/data/corporate/documents/LM-White-Paper-Intel-Driven-Defense.pdf.
- Cannady, James, and Jay Harrell. A Comparative Analysis of Current Intrusion Detection Technologies. Technical paper. Accessed July 15, 2016. http://www.scis.nova.edu/~cannady/TISC96.pdf.
- Ibid.
- Petry, Scott. “As Good As They’re Getting, Analytics Don’t Inherently Protect Data.” Dark Reading. February 2, 2016. http://www.darkreading.com/endpoint/as-good-as-theyre-getting-analytics-dont-inherently-protect-data–/a/d-id/1324139.
- Bailey, Tucker, Andrea Del Miglio, and Wolf Richter. “The Rising Strategic Risks of Cyberattacks.” McKinsey Quarterly. May 2014. http://www.mckinsey.com/business-functions/business-technology/our-insights/the-rising-strategic-risks-of-cyberattacks. (sidebar 1)



Leave a Comment