Ask an average person if they know what blockchain is and you’ll likely get a deer-in-the-headlights look. Ask the same person if they know about Bitcoin and their eyes light up. Cryptocurrencies, like Bitcoin, are the most widely recognized technologies leveraging blockchain today. Cryptocurrency markets dominate the media and many want to invest in them without any real understanding of the mechanics or stability of the technology or its theoretical foundations. The easiest way to sum up blockchain is that it is a mechanism to close the trust gap between geographically disparate parties by providing complete transparency and immutability with respect to the transactions being conducted. It’s important to remember that while blockchain technology enables cryptocurrencies, blockchain is not synonymous with cryptocurrency. A cryptocurrency depends on many elements including a blockchain, a wallet, and public key encryption.
The distributed ledger mechanism made possible by blockchain is so broadly applicable that it will enhance and improve the next generation of distributed and online services. Blockchain has the ability to decentralize choke points and ensure greater transparency than existing technologies. Whether the future of the Internet is artificial intelligence, virtual reality, semantic web or something else entirely, blockchain is well positioned to be a foundational element due to its rapid acceptance by the technology community. Blockchain is applicable to industries ranging from healthcare, law, finance, defense, music, and gaming to energy. The Bitcoin Shop, Inc. (BTCS) illustrates a variety of blockchain use cases as shown in Figure 1. Note, there is no singular “Blockchain,” and hence BTCS’ reference to “The Blockchain” is in error. Each industry, product or use case will have a unique blockchain implementation within its own distributed network.
Figure 1: Blockchain Uses (BTCS.com)
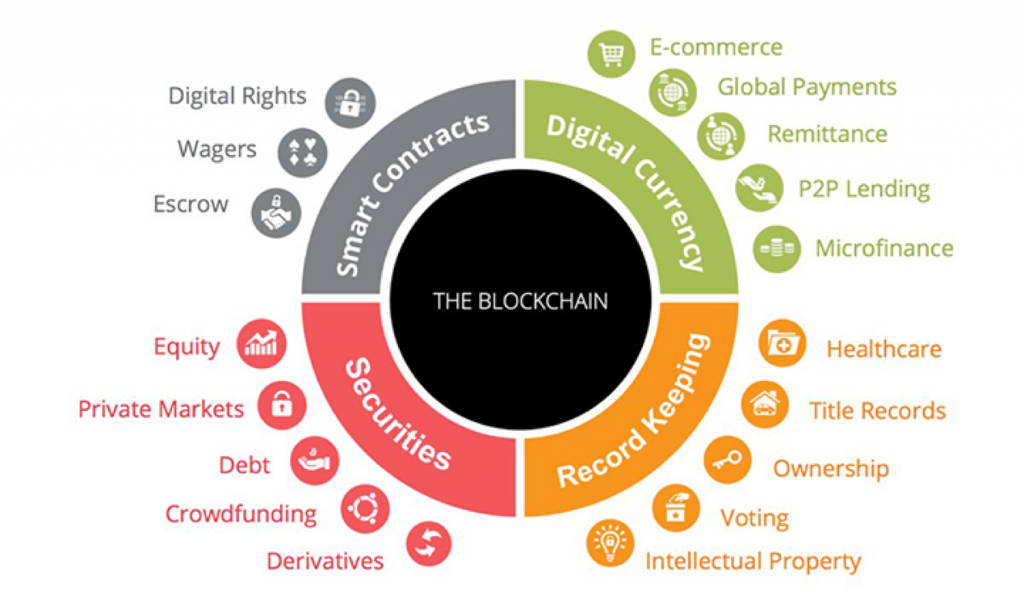
What makes blockchain so important? Blockchain is applicable to any industry, business or capability that requires some sort of transaction. This means that there is significant potential for blockchain to change the way transactional trust is established. Take health care as one example. Electronic Healthcare Records (EHR) are becoming more common and allow for a patient’s health record to move with them from provider to specialists and different hospitals around the world. The accuracy and integrity of the medical records is paramount to a patient’s safety. Blockchain would offer a level of certainty that the medical records are accurate and complete, providing a full history to help diagnose and treat patients. At the same time, blockchain eliminates the single point of trust failure found in conventional chain of trust schemes that revolve around certificates issued by certificate authorities.
Another area of concern is prescription medicine abuse and the opioid crisis plaguing the United States. A private prescription blockchain could record each and every prescription written as a transaction, enabling a reduction in the number of forged or fake prescriptions and traceability as to where and to whom medications are distributed. This won’t solve the opioid abuse problem but it would be a positive step in fighting the epidemic.
Blockchain could also be used to track and record voting. Imagine voters being able to vote from home, work or even their smartphone. No more need for polling stations or manual counts, and the uncertainty associated with inaccurate or tampered vote counts would be significantly reduced. Blockchain enables 100% transparency and ensures transactional integrity and non-repudiation across a distributed ledger. This means that every vote cast is accurately accounted for and is permanently recorded and cannot be tampered with. Essentially, every eligible voter would be issued one and only one token. When the voter uses their token (i.e., casts their vote) it is recorded in the blockchain ensuring the integrity of one vote per voter. In order to cast a vote, the token issued to each voter would be “spent” through an authentication process involving the voter’s private key, preserving the integrity of the process.
This all sounds good as long as blockchain does what it says it does and is as secure as everyone claims it to be. After all, the distributed ledger ensures transactional integrity right? What if this technology it uses is advancing faster than smart people who secure it can keep up with? The truth is that many blockchain applications are so new that malicious actors have only just started to look for ways to circumvent and subvert its integrity.
In a very short time, there have been several major breaches associated with blockchain (all within the cryptocurrency domain, e.g., Bitcoin). To be fair, blockchain technology itself has not been compromised. The breaches have stemmed from implementation issues with the overall cryptocurrency exchange ecosystems that used the Bitcoin blockchain. These range from poor service management to insider threat and theft via hacking. Attacks against Bitcoin exchanges have revealed multiple attack vectors and many more are likely to come. Attackers’ goals include the initiation of a blockchain transaction and subsequent fraudulent modification before the transaction is recorded to trick merchants into accepting the fraud before the necessary community consensus is achieved to register the transaction. Currently, there are five named attacks that have been identified:
- Majority attack
- Vector76 attack
- Finney attack
- Race attack and
- Alternative history attack
While these attacks have a low probability of successful execution, the majority attack is the most intriguing. Majority attacks operate against blockchain’s distributed consensus model. The premise is that an attacker or group of attackers gain control of the majority (greater than 50%) of a blockchain community. In that case, the attacker essentially controls the distributed ledger and could then confirm fraudulent transactions, such as double billing and double mining at will. Blockchain’s consensus model relies upon the notion that it is difficult or impossible to coordinate the subversion of a majority of participants at a given point in time. There are no provisions in blockchain that technically prohibit a dishonest group from controlling a majority of a blockchain.
Quantum Computing: Another concern with blockchain implementations such as cryptocurrencies is the impact that quantum computing may have. Post-quantum cryptography may end the utility of standard asymmetric cryptography algorithms such as RSA, or others based on difficult math problems including the factorization of large integers, discrete logarithms and elliptic curves. Google and NASA performed quantum computing testing against standard laptops in 2016 and found that at peak performance the quantum computers out-performed personal computers by 100 million times. However, as powerful as quantum computing may be, blockchain itself is relatively immune to it because blockchain relies on cryptographic hash algorithms and not asymmetric cryptography.
Quantum computing breaks technologies that rely on asymmetric cryptography such as cryptocurrencies whose wallets use public key cryptography to commit and validate transactions. Nearly all cryptocurrencies employ public key algorithms such as the Elliptical Curve Digital Signature Algorithm (ECDSA) and the Elliptical Curve Diffie-Hellman key agreement (ECDH), which are quantum-vulnerable. Blockchain, on the other hand, relies on secure hash algorithms, which can be quantum-proofed by simply increasing the output size.
Fortunately, quantum computers are not readily available and are currently cost prohibitive. However, experts say that they could be a major factor in as little as a decade. As noted above, quantum computing and post-quantum cryptography pose no real threat to blockchains, whose technical approach is to employ hashing to ensure integrity, not encryption to ensure confidentiality and authenticity. People are a more significant threat than quantum computing and, arguably more dangerous.
Implementations using blockchains can still be taken down by human interactions, technical flaws leading to vulnerabilities or insider threats. Many people are familiar with the Mt.Gox (Magic The Gathering Online Exchange) hack, and point to it as an illustration of blockchain vulnerabilities. The Mt.Gox hack was not a successful attack on blockchain but rather on the cryptocurrency exchange’s back end. The attack exploited a combination of poor management, poor testing and coding, and single point of failure (bottleneck) issues. Consequently, an attacker gaining control of an auditor’s laptop and was able to steal 850,000 bitcoins worth more than $450 million.
In 2016, the Decentralized Autonomous Organization (DAO), (effectively a venture capital fund for the cryptocurrency and decentralized application domain)was attacked. The DAO was a complex Smart Contract using the Ethereum network. To allow investors to leave the scheme, the DAO included something called the “split function.” This enabled users to retrieve funds (in Ethereum) invested in the DAO. If an investor wanted to pull out of the DAO, they would create a “Child DAO” and approve their proposal to send Ethereum to the original investment to an address after a period of 28 days. The hack came when an attacker exploited a vulnerability in the split function. When a split request was made, but before the transaction was registered, a recursive function transferred more Ethereum for the same DAO tokens. In the end $50 million worth of Ethereum was stolen. Again, the attack worked against a software vulnerability in the overall ecosystem, not against blockchain.
Like every new technology, blockchain is neither perfect nor completely secure. There will always be people looking for vulnerabilities and means to manipulate the technology in ways the developers never intended. Should we be skeptical of blockchain and its claim of being a completely secure and unchangeable permanent record (or ledger)? Absolutely! However, blockchain is a revolutionary capability that can alter how the many industries will think about the future of transactions.
Sources



Leave a Comment