In today’s world, people are always connected, and that is even more so with teenagers and young adults as they seek to solidify social circles. Positive relationships with friends can occur as a result, but the interaction with the device can often be the risky part. Learning upfront tips that while one seeks to expand their friendship, one must take active steps to maintain one’s privacy. This is critical. Many cybercriminals and predators exist on the internet. They infiltrate social media platforms, so the best way to protect oneself is to set the proper privacy settings on personal devices. Use these tips and get started!
What is Cybersecurity? Why Privacy?
Protection against criminals and/or protection against unauthorized use of digital data and the needed steps taken to achieve this security.
Why is Cybersecurity important?
- Helps protect your data and private information from being stolen by hackers.
- Can prevent identity theft and any resulting financial loss.
- Helps prevent spam and scam profiles from reaching you.
There are many simple ways to increase online security, including:
1. Check your apps to see what they have access to.
- Do your apps have access to the below?

Location

Microphone

Camera

Photos

Contacts
Image 1
- If the app does not require these things to function, they are most likely allowed for tracking purposes and are best disabled.
- For example, Snapchat is an app that uses the camera to take pictures. The pictures, which are used to type on and communicate with friends, meaning the camera feature is required and should be enabled.
- Snapchat has an optional map feature that you can enable or disable. While it can be fun seeing your friends’ locations, if they get hacked, there is the possibility of a random stranger having access to your location as well. This feature is fun, but an unnecessary security risk.
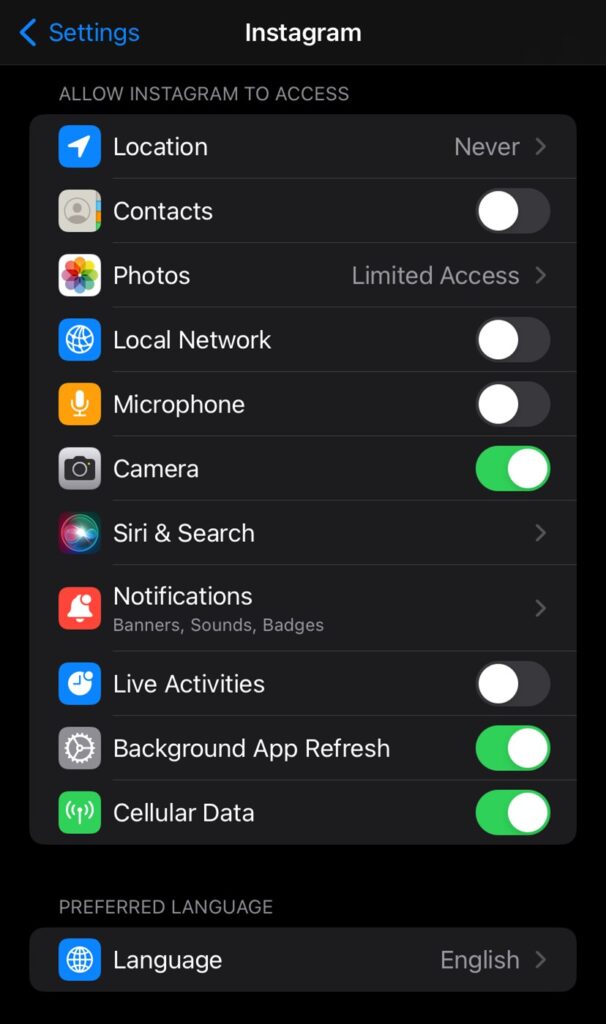
Image two displays what access Instagram has to certain functions. Instagram asks for location information, but this is not needed for functionality, therefore this is probably used to gather information and track the user.
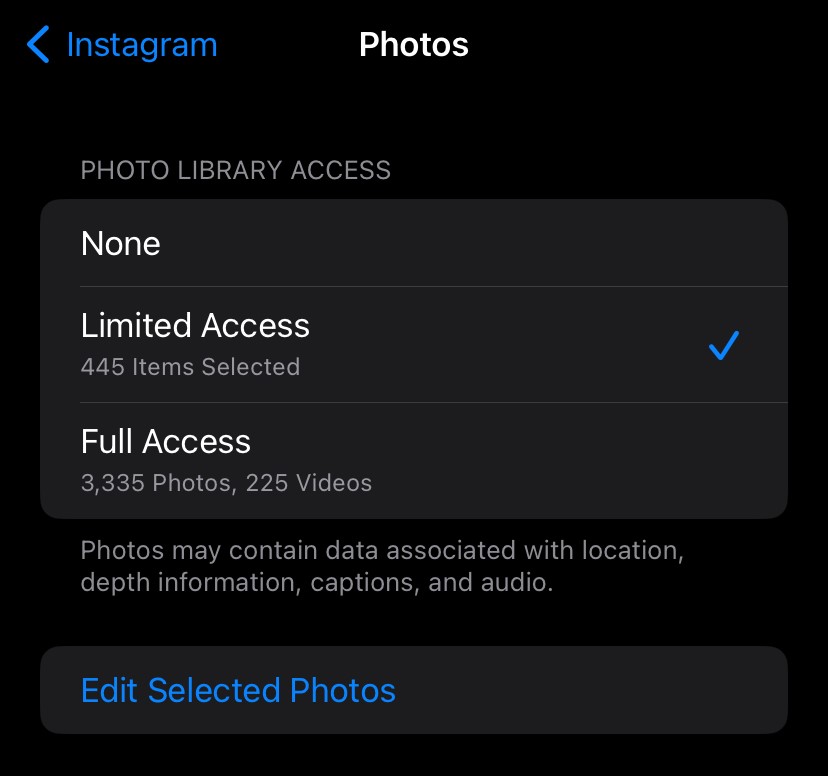
- If an app, such as Instagram or TikTok offers the ability to use photos in posts, the app will prompt you to “allow” access to photos, choose the option stating “Limited Access” so any photos with personal or private information attached, will not get leaked.
There are three options provided when photo access is viewed in settings on iPhone. Ensure that the option “limited access” is selected. This ensures these apps do not gain access to any sensitive photos that may be on your device.
2. Make sure any social media accounts you have are set to private especially if these accounts contain personal information or details about your life.


Image 4
If you use Facebook marketplace, only the object being sold should be in the picture. Make sure nothing personal ends up in the background.
If you’re selling anything outside, make sure there are no street signs in the background, and also make sure your house isn’t in the background. You do not want anyone to obtain your house number from the picture.
If you take a picture of an object you are selling while it’s resting on a surface (like a table) ensure there is no mail on that surface, as people may be able to obtain an address from the mail.

Snapchat

X (formerly Twitter)
Image 5
Understand what to look for with spam and fraud accounts:
- Blank profiles, especially ones with strange names
- Celebrity profiles that are not verified
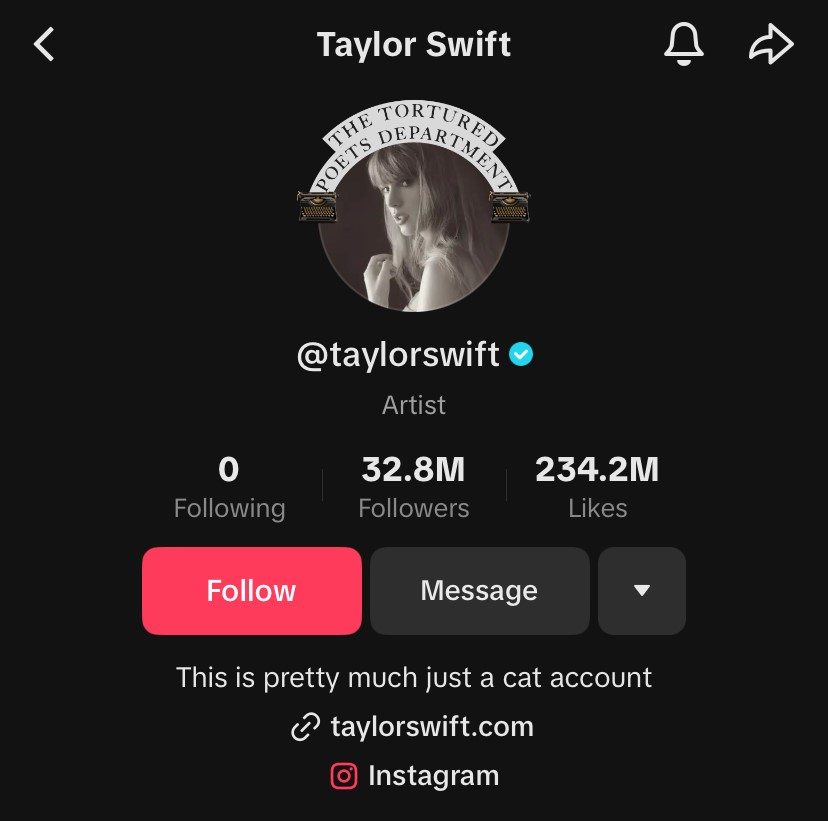
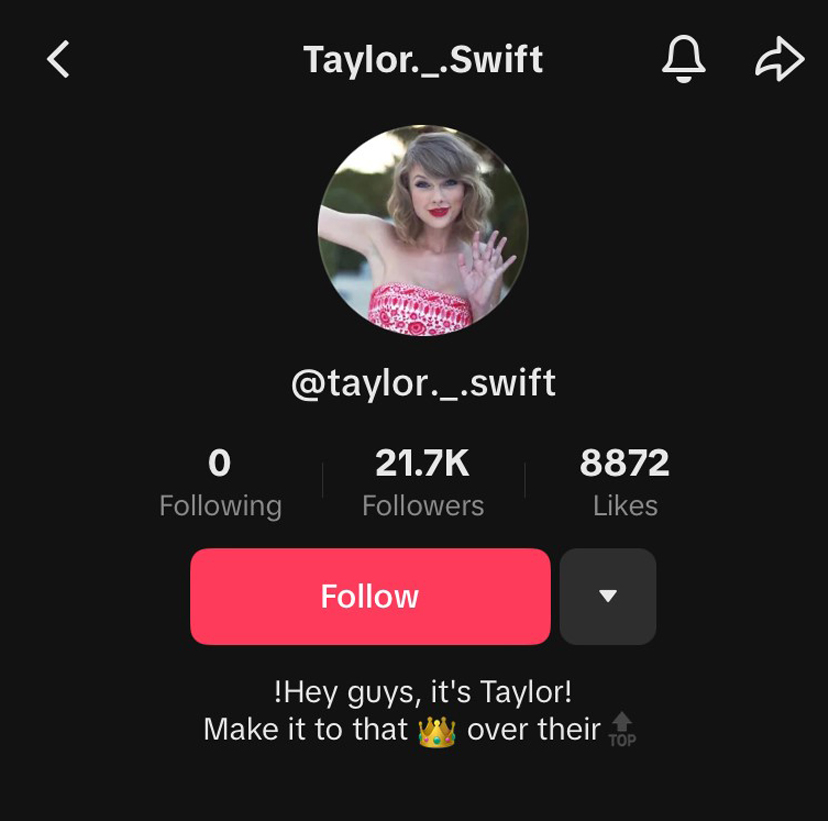
Note how, in image 6, there is a small blue circle with a check mark next to the username. This indicates a “verified account”, certifying that the celebrity is who they say they are. Accounts with celebrity names that do not have that app/site’s version of a verification mark are most likely fake and should not be trusted if they are reaching out to you.
Accounts that are exact replicas of friends/families who already follow you
- This is a common way for hackers to gain access to private account information and your friends list (this happened to some of my family members on Facebook)
- Sales or “special deals” messages from unverified accounts
3. Use Secure Messaging
Using a VPN:
- Useful in general in case anyone does gain access to your data, so they can’t determine your location, but especially useful when traveling, since you may have to use more public wifis and can prevent anyone who may have gained access to your location from following you.
VPN Examples: SOURCE
Below are three of the best rated VPNs, all include a 30-day free trials




- Has a more limited free version that can help college students, or unemployed high school students, looking to spend as little money as possible.
- The free version provides access to online content blocked in your country, unlimited bandwidth, and prevention of browsing tracking.
- Does not work for streaming services or browsing in numerous other countries, like their full version does.
4. Five Simple Cyber Privacy Tips:
- Do not use voice activated technology, such as:
- Amazon Echo/Alexa
- Siri
- In order for these devices to work they must have an active microphone on at all times so they can hear the keywords such as “hey Alexa” or “hey Siri” meaning that, should someone external gain access to the device, they would be able to hear every conversation you had in your home.
- Use home WiFi if possible
- Use a personal hotspot over public WiFi
- If you must use public WiFi, use a VPN or a secure browser like DuckDuckGo or Tor to get an extra layer of security layered over your work/ browsing.
- Check privacy policies before accepting anything
- Many companies may try to hide small things in their privacy policy, so it is best to know all the details of what you are accepting.
- To understand the privacy policy/ terms of service better, you can search for videos online explaining everything they include, as those are often available.
- When using websites, ensure the URL starts with HTTPS not HTTP
- HTTPS has an extra layer of security
- HTTPS stands for Hypertext Transfer Protocol Secure while HTTP just stands for Hypertext Transfer Protocol
- Disable cookies
- When a website prompts for cookie usage, look at what they are asking for and alter settings so only mandatory cookies are used
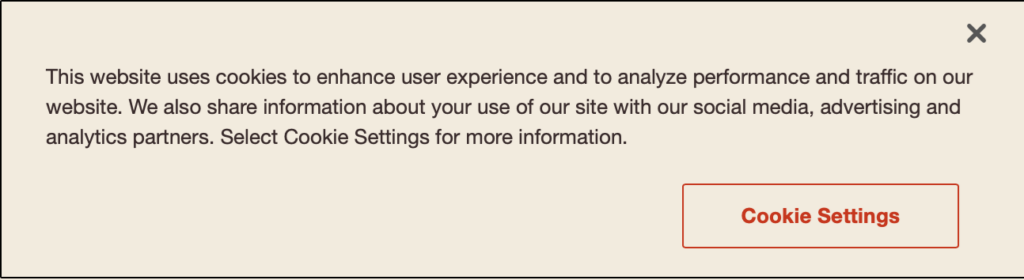
This is an example of Burger King’s cookie policies. You can gain better protection and more control by clicking cookie settings and turning off whatever cookies you can, instead of just accepting.
Be confident in yourself and in your online behaviors, so you can stay in control of your privacy and your life. These tips should get you started! Stay Cyber Safe! ![]()
Diane M Janosek, PhD, JD, CISSP, LPEC




Leave a Comment